QNAP issues “take immediate actions” statement for DeadBolt ransomware

QNAP users are being targeted by another ransomware attack.
On January 26, 2022, QNAP issued a statement to immediately stop your NAS from being exposed to the internet. Instructions to disabling internet access can be found in the official statement from QNAP.
QNAP NAS owners have been targeted lately with multiple ransomware attacks in the last few years. Qlocker, eCh0raix, and now DeadBolt.
DeadBolt ransomware
The DeadBolt ransomware group started encrypting QNAP NAS devices worldwide, using a zero-day vulnerability found in the device software.
Files that get encrypted are renamed with a .deadbolt file extension.
The ransomware will also hijack the QNAP device log-in page with a message that says “WARNING: YOUR FILES HAVE BEEN LOCKED BY DEADBOLT”.
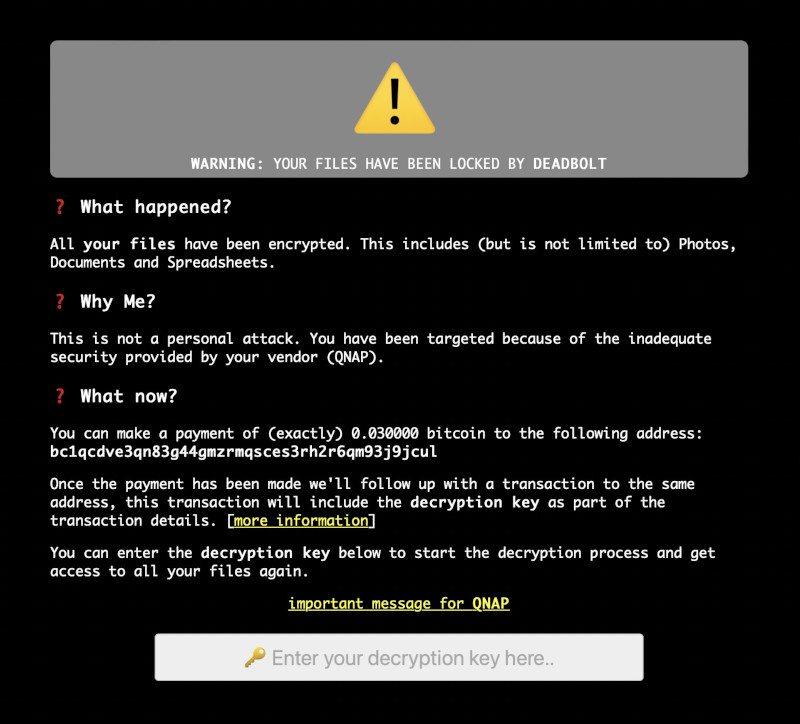
The message informs you that your files are encrypted and requests payment of 0.03 bitcoin ($1,100) in exchange for the decryption key to unlock your files.
Master key for 50 bitcoin
The DeadBolt ransomware gang is offering the full details of the vulnerability to QNAP if they pay them 5 bitcoin ($184,000).
They are also claiming that there is a master key that can be used to decrypt all files for any affected victims. The cost for the master is 50 bitcoin ($1.85 million).
Forced Updates Controversy
On January 26th, QNAP forced a firmware update to v5.0.0.1891 for all of their customers.
This was with the belief that this firmware version had a fix for the vulnerability being used by DeadBolt.
But a QNAP customer with the latest 5.0.0.1891 firmware reported they were hit with this ransomware. QNAP later conceded that there could be another vulnerability exploited by the DeadBolt ransomware group.
QNAP also is saying that the forced firmware update should only have been installed by those who had the “Recommended version” setting enabled in the Auto Update setting of the NAS.
However, customers are claiming that they got this forced update even though that specific setting was not enabled.
Lessons Learned
If history has taught us anything, we cannot rely on the vendor’s software to provide protection of our data. We need to implement our own security and have data backups for any files that are important to us.
References: Bleepingcomputer, Twitter, The Record, ZDNet



